Designing ERP Security Roles that Work: A Governance Approach to D365 Finance

Introduction — Why Security Role Design Is a Governance Issue
Many organizations treat ERP security as a technical step done late in the project.
In reality, security design reflects organizational accountability — it defines who can act, who can approve, and who is accountable for what.
A poorly structured model leads to audit issues, segregation-of-duties conflicts, and operational bottlenecks.
From a governance perspective, security is not just about access control — it’s about defining responsibility lines across business and system layers.
→ For deeper foundational governance practices, also see SoD Conflicts & Audit Risks in D365 Finance.
https://www.fitgapfinance.com/d365-finance-sod-risks-audit/
The Governance Lens: Three Dimensions of Security
- Strategic level – defines decision-making authority (CFO, Controller, Procurement Director).
- Functional level – defines who executes and reviews (Accountant, Buyer, AP Clerk).
- System level – defines what the system allows (roles, duties, privileges).
When these three layers align, ERP access supports business integrity and transparency rather than undermining it.
Principles of a Well-Governed Security Model
1. Clarity of Authority
A clear Delegation of Authority (DoA) document should be available to the project team.
However, what’s documented may differ from what happens in reality — some directors might request additional approvals or manage exceptions outside the ERP.
Reconciling policy vs. practice early helps prevent confusion during testing and go-live.
2. Segregation of Duties (SoD)
Organizations should provide a documented SoD matrix identifying incompatible role combinations.
This matrix guides both security design and workflow validation to ensure proper control across processes.
→ For practical examples of high-risk conflicts, see 10 High-Risk SoD Conflicts Auditors Flag in D365 Finance.
https://www.fitgapfinance.com/d365-finance-sod-risks-audit/
3. Audit Alignment
Involve internal and external auditors early.
They often have expectations about SoD assurance, user-access reports, and change logs.
Their feedback ensures your design meets audit standards and avoids rework later.
→ Audit requirements also influence data migration and reconciliation — see Data Migration Mistakes to Avoid in D365 Finance.
https://www.fitgapfinance.com/data-migration-in-dynamics-365-how-to-avoid-the-most-costly-mistakes/
4. Data Governance & Privacy
Security is also about data visibility.
Clarify what data users can and cannot access — especially in sensitive areas like payroll or vendor bank details.
When possible, try to limit row-level security as this adds an additional layer of complexity.
→ This ties directly into reporting integrity — see Ledger vs Subledger in D365 Finance for how data visibility affects reconciliations.
https://www.fitgapfinance.com/ledger-vs-subledger-d365-finance/
5. Document & Attachment Security
Don’t underestimate the risk of attachments.
Access to supporting documents (SharePoint, OneDrive, etc.) must mirror ERP access rules.
Ensure folders and libraries inherit the same role hierarchy to avoid data leaks.
6. Automation Governance
In many ERP implementations, some steps are automated — for example, automatically creating a purchase order from an intercompany sales order.
Confirm whether the organization is comfortable with such automations and understands their governance implications.
Automation can accelerate processes but may bypass manual approvals, altering accountability and SoD expectations.
These cases must be documented and reflected in both security design and control frameworks.
→ Workflow rules are often impacted as well — see Workflow Best Practices Every Company Should Follow in D365 Finance.
https://www.fitgapfinance.com/d365-finance-workflow-best-practices/
7. Scalability & Sustainability
Design roles by business function, not by individual.
Review and adjust regularly as responsibilities evolve.
8. Traceability
Every critical approval or override should leave a digital trace.
Auditability is not an afterthought — it’s a foundation of ERP governance.
A Governance-Based Role Structure Example
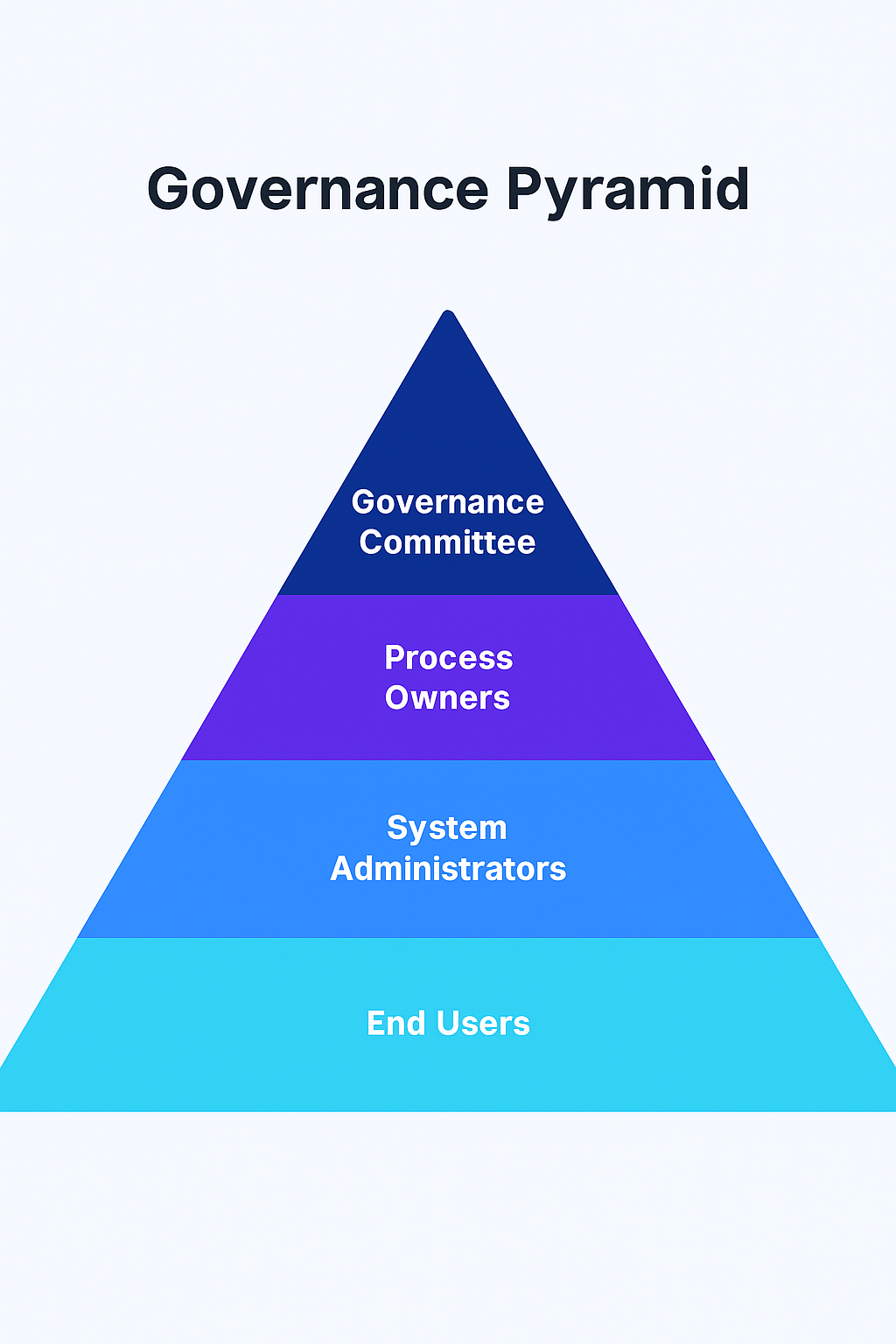
A three-level pyramid illustrating:
- Governance Committee (approves the framework)
- Process Owners (define duties and approvals)
- System Administrators (configure roles and privileges)
- End Users (assigned by responsibility)
This hierarchy ensures top-down accountability with bottom-up feedback loops.
Linking Security to Licensing Optimization
A well-designed role model helps right-size licensing.
For example, approvers who don’t create transactions can often use Activity or Team Member licenses rather than full ones — reducing cost without reducing control.
This governance-driven design approach creates tangible financial value for CFOs.
Conclusion — Elevating Security Design to a Leadership Conversation
Security design is not just an IT topic — it’s a leadership conversation about trust, accountability, and efficiency.
Organizations that design roles through a governance lens gain stronger control, lower costs, and better collaboration between business and IT.
→ For governance roles across the full project lifecycle, see Roles & Responsibilities in an ERP Implementation Project.
https://www.fitgapfinance.com/roles-responsibilities-in-an-erp-implementation-project/



